#Breaking: Supermarket in Kharkiv, east Ukraine – all payment terminals look to have been hit by the #Petya #ransomeware pic.twitter.com/e1nUHNkVwg
— Ryan Clapham (@NewsReport365) June 27, 2017
The most recent cyber attack “Petya/Petrwrap/ExPetr’ or ‘GoldenEye’” has quickly infected to windows systems all over the world, crippling large firms across the US, Europe, Israel, Russia Ukraine. A variant of Petya was first discovered in March 2016 which propagated via infected e-mail attachments. The latest variant of Petya was seen in June 2017, which is used for global cyber attack, primarily targeting Ukraine.
You will get a message like below once your system infected and encrypted the files
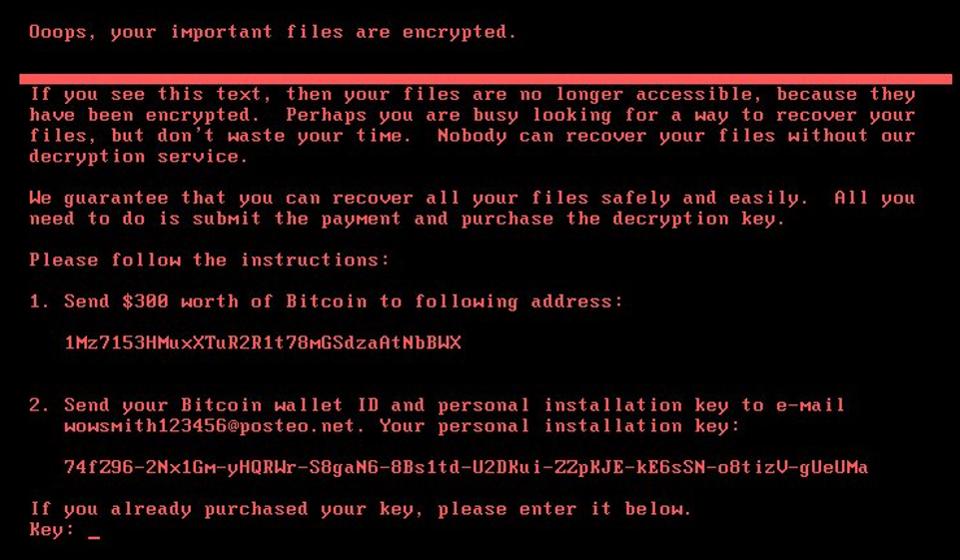
Ransomware is a dangerous software that destroys the victim’s system and it threatens to publish or delete the data till a ransom in digital currency (usually in Bit coins) is payed. WannaCry was the last major ransomware attack that infected the systems in May.
Petya is very similar to WannaCry, but it is more dangerous than WannaCry. The affected systems will be fully encrypted and all the information in the machine becomes completely inaccessible. Target of the attack is Microsoft Windows Systems. Unlike a usual ransomware it doesn’t just encrypt your file, it overwrites and encrypts the NTFS file table.
Colin Hardy is showing some very quick analysis of Petya / Petrwrap Ransomware in his malware lab.
How does Petya Ransomware works?
Ransomware take over a computer and demand for $300 (paid in Bitcoin) to release it. Once a computer is infected, the Petya Ransomware can rapidly spread across an organization using Eternal Blue vulnerability in Microsoft Windows or through to Windows administrative tools. The malicious Petya ransomware tries one option, if that option doesn’t work, then tries the next one. Ryan Kalember, of cyber security company Proof point said: “It has a better mechanism for spreading itself than WannaCry.”
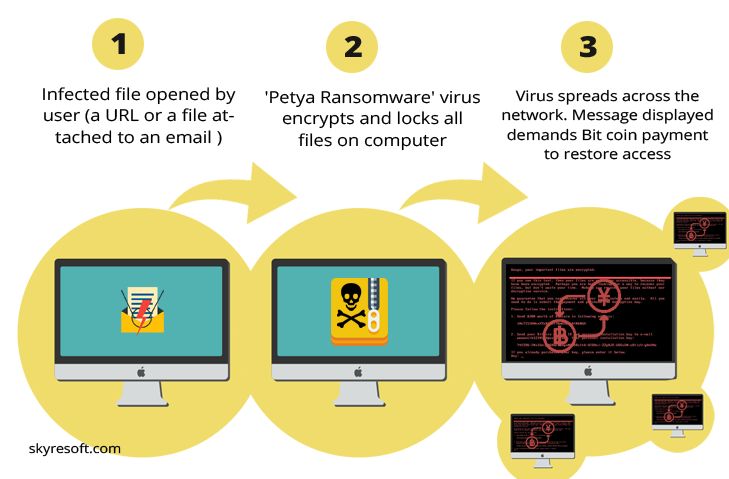
How wide is the damage?
Petya can attack or hit around 2,000 countries including UK, US, France and Germany. Public organizations were also infected, with the global advertising giant WPP and the Ukraine National Bank both reporting malware attacks. Ukraine as the most affected country and as a precautionary measure, the Chernobyl nuclear power plant systems were reportedly switched to manual.
What to do to be protected?
For protecting our system from Petya ransomware, immediately install the MS17-010 from Microsoft, it is one of the foremost things to do if not yet done.
- Do not open emails from strangers and do not ever click on the attachments until you recognize the sender.
- If something strange is occurring on your system and you need assistance, immediately reach out your IT help desk.
- Try not to open non-urgent attachments, even friendly sources could be infected.
- Update anti-virus on your device and run a scan
- Norton products and Systematic Endpoint Protection (SEP) can proactively protect customers from attempting to spread Petya using EternalBlue.
- SONAR behavior detection technology can also proactively protect against infections.
If your computer has been infected, or if you get a screen that remotely resembles the snippet at the start of the post, immediately turn your computer off, disconnect it from your network.